
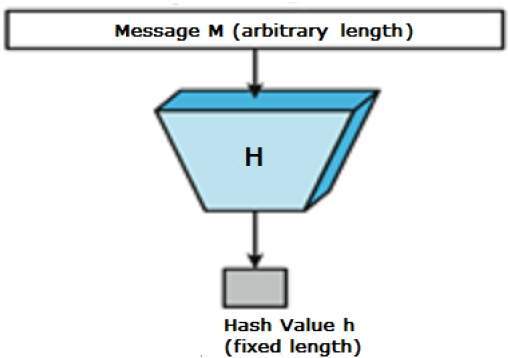
The key used in public encryption is based on a hash value. This is a value that is generated from a base input number that makes use of a hashing algorithm. The important thing to know about a hash value is that it is almost impossible for the original input number to be found out without knowing the data used to form the hash value.
......
A hashing algorithm is a cryptographic hash function that maps data of random size to a hash of a specific size. Although they have been designed to be a one-way function impossible to invert, a lot of hashing algorithms have been compromised in time.
Cryptographic hashes are used mostly in IT for digital signatures, password storage, file verification systems, message authentication codes and other types of authentication.
They can also be used for indexing data in hash tables, for fingerprinting, identifying files, or detecting duplicates. The basic idea is to use a deterministic algorithm that takes in one input and generates a fixed length string every time. As a result, the same input will always give the same output.
......

留下你的回應
以訪客張貼回應